SPNEGO (Simple and Protected GSSAPI Negotiation Mechanism) is used to authenticate transparently through the web browser after the user has been authenticated when logging in the desktop session.
Before going deeper into how to integrate SPNEGO with eXo Platform, see the below typical usecase:
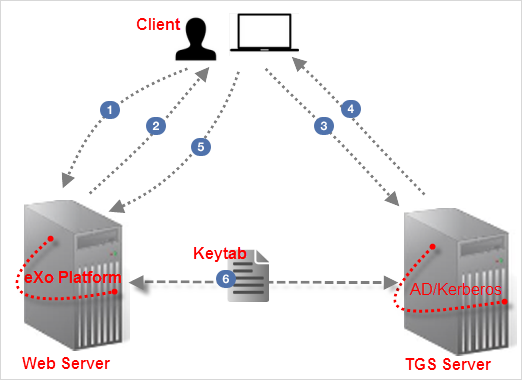
In particular:
 The User logs into the desktop that is governed by a Ticket Granting Service (TGS) (such as Active Directory for Windows or Kerberos Server for Linux),
then opens a browser (for example, Firefox) to access the web application hosted on eXo Platform.
The User logs into the desktop that is governed by a Ticket Granting Service (TGS) (such as Active Directory for Windows or Kerberos Server for Linux),
then opens a browser (for example, Firefox) to access the web application hosted on eXo Platform. The browser transfers the desktop sign-on information to the web application.
The Web Server will respond presenting that it must "negotiate authentication".
If both the browser and the server support SPNEGO, it will be used.
The browser transfers the desktop sign-on information to the web application.
The Web Server will respond presenting that it must "negotiate authentication".
If both the browser and the server support SPNEGO, it will be used. The browser then contacts a Kerberos Ticket Granting Service (TGS) to request a Service Ticket (ST).
This Service Ticket is used to prove the identity of the caller.
The browser then contacts a Kerberos Ticket Granting Service (TGS) to request a Service Ticket (ST).
This Service Ticket is used to prove the identity of the caller. The TGS Server generates a ST, then returns it to the client.
The TGS Server generates a ST, then returns it to the client. The ST is then sent to the Web Server.
The ST is then sent to the Web Server. The Web Server that is configured within TGS to be a Service Principal (SP) uses a keytab file to communicate with the TGS for authenticating the user.
The Web Server that is configured within TGS to be a Service Principal (SP) uses a keytab file to communicate with the TGS for authenticating the user.
For simplification, the SPNEGO integration with eXo Platform involves specific activities that need to be performed on 3 factors:
Machine 1: A server that runs the TGS (Active Directory/Kerberos Server) and associated Kerberos Key Distribution Center (KDC).
Machine 2: A server on which eXo Platform is running.
Machine 3: The end-user client that has a browser installed.
The implementation of a Single Sign-On for HTTP requests using the SPNEGO web authentication is not the same in different environments, so consult the relevant documents. In this guideline, detailed instructions for 2 common environments, including Windows and Linux, will be covered. However, regardless of your using environment, the following main steps are generally required: